Government abstract
Whereas most finish customers are well-acquainted with the risks of conventional phishing assaults, equivalent to these delivered by way of electronic mail or different media, a big proportion are doubtless unaware that Microsoft Groups chats may very well be a phishing vector. Most Groups exercise is intra-organizational, however Microsoft allows Exterior Entry by default, which permits members of 1 group so as to add customers exterior the group to their Groups chats. Maybe predictably, this function has offered malicious actors a brand new avenue by which to take advantage of untrained or unaware customers.
In a current instance, an AT&T Cybersecurity Managed Detection and Response (MDR) buyer proactively reached out with considerations a few consumer who was exterior to their area sending an unsolicited Groups chat to a number of inner members. The chat was suspected to be a phishing lure. The client offered the username of the exterior consumer in addition to the IDs of a number of customers who had been confirmed to have accepted the message.
With this data, the AT&T Cybersecurity MDR SOC staff was in a position to determine the focused customers, in addition to suspicious file downloads initiated by a few of them. A evaluation of the techniques and indicators of compromise (IOCs) utilized by the attacker confirmed them to be related to DarkGate malware, and the MDR SOC staff was in a position to head off the assault earlier than any important injury was carried out.
Investigation
Preliminary occasion evaluation
Indicators of compromise
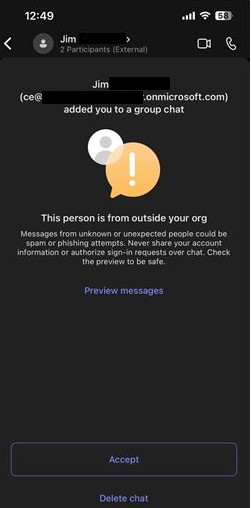
The client offered the under screenshot (Picture 1) of the message that was obtained by one in all their customers and which was suspected to be a phishing lure. An necessary element to notice right here is the “.onmicrosoft.com” area identify. This area, by all appearances, is genuine and most customers would most likely assume that it’s professional. OSINT analysis on the area additionally reveals no experiences for suspicious exercise, main the MDR SOC staff to imagine the username (and probably your entire area) was doubtless compromised by the attackers previous to getting used to launch the phishing assault.
Picture 1: Screenshot from buyer of obtained message
![teams message]()
Expanded investigation
Occasions search
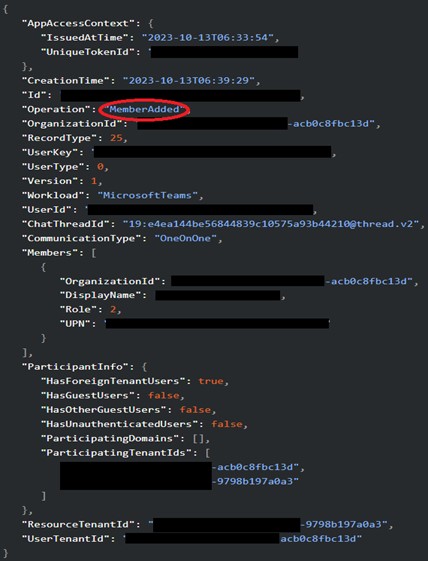
Performing a search of the exterior username within the buyer’s setting led the MDR staff to over 1,000 “MessageSent” Groups occasions that had been generated by the consumer. Though these occasions didn’t embody the IDs of the recipients, they did embody the exterior consumer’s tenant ID, as displayed in Picture 2 under.
Picture 2: Occasion log displaying exterior consumer tenant ID
![Teams event log]()
A Microsoft 365 tenant ID is a globally distinctive identifier assigned to a company. It’s what permits members of various firms to speak with each other by way of Groups. So long as each members of a chat have legitimate tenant IDs, and Exterior Entry is enabled, they will change messages. With this in thoughts, the MDR SOC staff was in a position to question occasions that contained the exterior consumer’s tenant ID and located a number of “MemberAdded” occasions, that are generated when a consumer joins a chat in Groups.
Picture 3: “MemberAdded” occasion
![member added]()
These occasions embody the sufferer’s consumer ID, however not the exterior consumer ID. Along with the exterior tenant ID, the MDR SOC staff was in a position to positively hyperlink these “MemberAdded” occasions again to the attacker by way of the “ChatThreadId” subject, which was additionally current within the authentic “MessageSent” occasions. The client was supplied with a listing of customers who accepted the exterior chat and was then in a position to start figuring out probably compromised belongings and accounts for remediation.
Occasion deep-dive
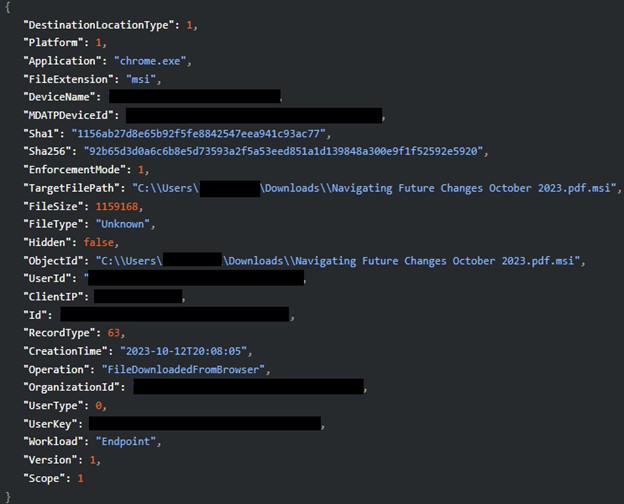
The MDR SOC staff continued to drill down on the phished customers to find out the exact nature of the assault. They subsequently found three customers who had downloaded a suspicious double extension file. The file was titled “Navigating Future Adjustments October 2023.pdf.msi” (Picture 4).
Picture 4: Suspicious double extension file obtain
![suspicious download]()
Double extension information are generally utilized by attackers to trick customers into downloading malicious executables, because the second extension, .msi on this case, is normally hidden by the filesystem. The consumer believes they’re downloading a PDF for enterprise use, however as a substitute receives a malicious installer.
The MDR SOC staff was in a position to present the filename and related hashes to the shopper who in flip handed that data onto their endpoint detection and response (EDR) supplier so the file may very well be added to the blocklist. The details about the file downloads additionally enabled the shopper to start figuring out affected belongings for isolation and remediation.
Reviewing for added indicators
The client later offered the malicious file to the MDR SOC staff for additional evaluation. Upon detonation in a sandbox, the file tried to beacon out to the area hgfdytrywq[.]com, which is a confirmed DarkGate command-and-control (C2) area, in keeping with Palo Alto Networks (https://github.com/PaloAltoNetworks/Unit42-timely-threat-intel/blob/main/2023-10-12-IOCs-for-DarkGate-from-Teams-chat.txt). The filename can also be similar to the information listed by Palo Alto Networks and the double-extension file is a recognized DarkGate tactic.
Remediation
The MDR SOC offered the shopper with a listing of customers who had obtained the message, customers who had been confirmed to have accepted the message, and customers who had been recognized as having initiated a obtain of the malicious .msi file. The client used this data to provoke password resets for the affected customers and to find out which belongings had been contaminated in order that they may very well be remoted and rolled again to a clear state. The DarkGate file hashes and paths had been blocklisted by the shopper’s EDR answer and the C2 area was blocked. The client was additionally suggested to think about disabling Groups Exterior Entry except it was obligatory for enterprise use.
Suggestions
E-mail phishing assaults have lengthy been a risk to organizations, and they’re going to proceed to be, however phishing by way of Microsoft Groups is a comparatively new phenomenon. This assault vector is a reminder of the necessity for fixed vigilance and consumer coaching within the face of evolving threats.
Except completely obligatory for each day enterprise use, disabling Exterior Entry in Microsoft Groups is advisable for many firms, as electronic mail is usually a safer and extra intently monitored communication channel. As all the time, finish customers ought to be educated to concentrate to the place unsolicited messages are coming from and ought to be reminded that phishing can take many varieties, past the standard electronic mail. Not everyone seems to be on the identical staff!