Govt abstract
Multifactor authentication, or MFA, gives customers with an added layer of safety when logging into internet functions. Surpassing its predecessor, two-factor authentication, in 2023, MFA is a normal choice for one more layer of safety for on-line accounts. .
In Might 2022, the Cybersecurity & Infrastructure Safety Company (CISA) revealed safety advisory AA22-074A describing how default configurations inside MFA functions are thought-about a vulnerability. The tactic was utilized by Russian state-sponsored cyber actors as early as Might 2021 in a profitable compromise of a US group.
Based mostly on this steerage from CISA, the AT&T Cybersecurity managed detection and response (MDR) safety operations middle (SOC) proactively scanned throughout our buyer fleet and found a buyer that was utilizing the default configuration, which could be exploited. SOC analysts contacted the shopper to tell them in regards to the threat and offered suggestions on find out how to safe their community.
Investigation
Occasions search
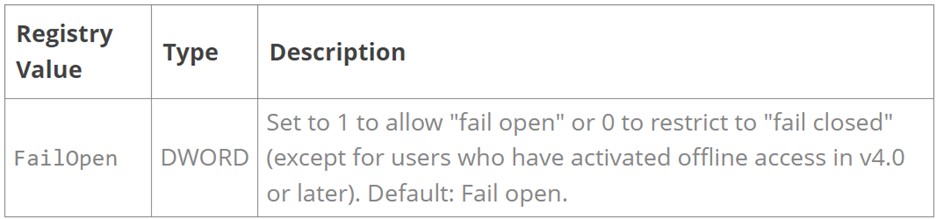
Analysts used the open-source instrument, Elastic Stack, to go looking our clients for “FailOpen,”which is the default configuration inside MFA functions that makes unauthorized entry attainable.
![ElasticStack open source]()
Occasion deep-dive
The search revealed a buyer with their MFA software set to FAILOPEN = 1, which is the setting that permits for a malicious actor to bypass authentication when exploited. The “FailOpen” setting permits for an incorrect try at a connection, which might then allow unfettered entry to an account with this setting on the shopper community.
![FailOpen]()
Reviewing for added indicators
From there, SOC analysts pivoted to looking out the shopper setting for any info that will establish related buyer belongings and accounts and that will point out outwardly malicious exercise. They found that the consumer accountable was listed as an administrator throughout the buyer setting.
![user responsible]()
![source asset]()
Response
Constructing the investigation
The analysts opened an investigation to deal with the misconfiguration within the MFA cellular software in addition to to substantiate whether or not or not the exercise related to the recognized consumer was licensed. Included within the investigation was a proof of the vulnerability in addition to a abstract of the concerned consumer’s exercise on the recognized belongings over the past 30 days.
![mfa analysis]()
Buyer interplay
Analysts created a low-severity investigation, which on this case meant that they weren’t required to contact the shopper. (Our MDR clients decide when and the way the SOC communicates with them.)
Nevertheless, to make sure that the problem was addressed in a well timed method, the analysts additionally notified the shopper’s assigned risk hunter group, “The ForCE,” and the investigation was reviewed and addressed by the shopper.
![mfa customer interaction]()
Finally, the investigation didn’t uncover any malicious occasions regarding the misconfiguration, but it surely illustrates how the AT&T MDR SOC shouldn’t be solely reactive but additionally works proactively to guard our clients.