As organizations develop and extra endpoints are added throughout the enterprise, they create an more and more broad assault floor refined attackers wish to compromise. In accordance with the 2019 Endpoint Safety Traits Report 70% of breaches originate on the endpoint¹. That’s probably as a result of endpoints usually characterize the Intersection between people and machines creating susceptible factors of entry for cybercriminals. This is the reason it’s more and more necessary to safe your endpoints.
Progress in endpoints
An endpoint is outlined as any computing gadget that communicates backwards and forwards with a community to which it’s related. Some finish consumer units function an interface with human customers whereas others are servers that talk with different endpoints on the community. Conventional endpoints started as bodily units together with servers, workstations, desktops, and laptops, all related to a company community. When smartphones and tablets turned handheld computing units with entry to company e mail, doc sharing and collaboration instruments the variety of endpoints a minimum of doubled.
Then got here the rise of the Web of Issues (IoT) together with units like printers, webcams, smartwatches, and thermostats, all of that are related to the community. Industries like healthcare and manufacturing are utilizing hundreds of thousands of IoT sensors to gather and alternate information. This continued progress in IoT solely will increase the variety of endpoints that must be protected.
One other contribution to the expansion in endpoints is the migration to the cloud. It’s estimated that 67% of enterprise infrastructure is cloud-based². This cloud transformation is the evolution from bodily units to virtualization and containerization.
Endpoint virtualization
The cloud is a multi-tenant setting the place a number of customers run providers on the identical server {hardware}. Virtualization and containerization are each virtualization applied sciences that separate the host working system from the packages that run in them.
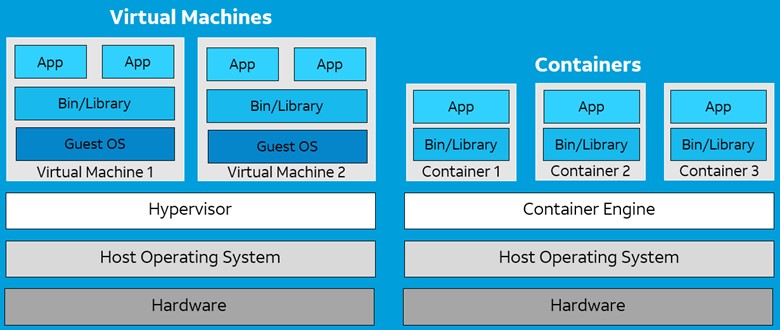
Virtualization is achieved utilizing a hypervisor, which splits CPU, RAM, and storage sources between a number of digital machines (VMs). Every VM behaves like a separate pc that will get a visitor working system and every VM is unbiased of one another. This enables organizations to run a number of OS situations on a single server.
Containerization, then again, runs a single host OS occasion and makes use of a container engine to assist bundle purposes into container photos that may be simply deployed and re-used. By splitting every particular person software operate or microservice into containers they’ll function independently to enhance enterprise resilience and scalability. Kubernetes then manages the orchestration of a number of containers. VMs and containers current very completely different safety challenges so let’s take a look at the evolution of endpoint safety and the options that meet the wants of advanced buyer environments.
Securing endpoints
For many years, organizations have closely relied on antivirus (AV) software program to safe endpoints. Nevertheless, conventional antivirus labored by matching identified malicious signatures in a database and may now not defend in opposition to at this time’s refined threats. Fashionable endpoint safety options are much less signature-based and way more behavior-based. Endpoint safety platforms (EPP) supply cloud native architectures that present a layered protection in opposition to fileless assaults utilizing machine studying and behavioral AI to guard in opposition to malicious exercise. Endpoint detection and response (EDR) options went past safety by recording and storing endpoint-system degree behaviors to detect malicious threats.
EDR options use information analytics mixed with menace intelligence feeds to offer incident responders with the forensic information for finishing investigations and menace looking. Along with blocking malicious exercise and containing the incident EDR options allow companies to reply and remediate threats. Endpoint safety continues to evolve with options together with IoT discovery and options to guard cell units.
Cellular safety is one in every of, if not the only most necessary aspect of enterprise safety being neglected at this time. Cellular menace protection (MTD) prevents or detects threats on cell units throughout the online, purposes, the gadget, and the community. Phishing is the commonest cell menace and phishing safety retains customers protected from being lured to malicious web sites the place attackers ship malicious downloads or inject code onto a tool.
App evaluation makes use of numerous strategies together with anti-malware filtering, code emulation, software reverse engineering, and dynamic app safety testing to detect malware or dangerous apps that might expose delicate information. System vulnerabilities or privilege escalations are recognized by monitoring OS variations, system parameters, gadget configurations, and system libraries. MTD additionally analyzes community connections to detect a compromised Wi-Fi community for malicious habits or checking for invalid certificates to forestall man-in-the-middle assaults. Cellular safety is not only a “good to have” resolution however changing into extra of a “will need to have” resolution, which can be changing into the case for cloud safety.
Cloud workload safety platform (CWPP) gives visibility and safety for a spread of workloads together with digital machines, digital servers, and containers in Kubernetes clusters. CWPP detects runtime threats on the VM and container degree, offering visibility and the cloud metadata wanted for incident response. These platforms can enhance effectivity by offering analytics and reporting which allow cloud engineers to optimize and scale software capability primarily based on demand.
Integrating CWPP with cloud safety posture administration (CSPM) options gives broader visibility whereas integration with the DevOps CI/CD pipeline construct course of helps defend machines all through the software program lifecycle. CWPP protects delicate information utilizing controls like information encryption, which frequently helps organizations meet some compliance and regulation requirements. Flexibility and scalability are necessary concerns when choosing a CWPP to assist a company’s present and future cloud infrastructure together with public, non-public, and hybrid cloud environments.
As expertise advances and the variety of endpoints develop so does the potential assault floor for cybercriminals to use. These transformations will compel endpoint safety distributors to proceed delivering modern options sooner or later.
¹Absolute | 2019 Endpoint Safety Traits Report
²SaaSworthy | Cloud Computing Statistics in 2023


