Information is energy and collaboration is essential for organizations to constantly adapt and enhance their safety measures as a way to keep forward of cybercriminals. An efficient method to keep forward is by enhancing a corporation’s safety posture by cybersecurity menace intelligence sharing. By exchanging details about potential and current cyber threats with different organizations, people, or entities, organizations can higher perceive the menace panorama and make knowledgeable choices about their safety methods. On this article, we are going to discover what menace intelligence sharing is and supply steering on beginning your personal program.
How menace intelligence sharing works
Menace intelligence sharing might be in comparison with a neighborhood watch program, the place group members collaborate and share details about suspicious actions, potential threats, and crime incidents to enhance the general security and safety of the neighborhood.
![security zone]()
Equally, menace intelligence sharing is a collaborative course of that allows organizations to alternate info equivalent to indicators of compromise (IoCs), ways, methods, and procedures (TTPs), and vulnerabilities between one another. It entails gathering menace intelligence from numerous sources, equivalent to inner community logs, safety instruments, open-source intelligence (OSINT), business menace intelligence feeds, and industry-specific sharing communities like Information Sharing and Analysis Centers (ISACs).
The collected knowledge is then analyzed to establish patterns, tendencies, and actionable insights, which assist organizations perceive the menace panorama and make knowledgeable choices about their safety methods.
Addressing menace intelligence sharing authorized, regulatory, and privateness considerations
To keep up privateness and foster collaboration, organizations ought to set up clear tips and use standardized protocols like Structured Threat Information Expression (STIX) or Trusted Automated eXchange of Indicator Information (TAXII) when sharing menace intelligence exterior the corporate. This collaborative strategy will in the end enhance the safety posture of all collaborating organizations.
Additionally, collaborating organizations ought to work intently with authorized and compliance groups to grasp the necessities and set up tips for sharing menace intelligence whereas adhering to knowledge privateness rules and industry-specific compliance requirements. Pointers ought to embody sanitization, anonymization, and encryption methods to guard delicate info from being publicly disclosed.
How menace intelligence knowledge is structured
Standardized codecs and languages, equivalent to STIX or TAXII, are used to construction the information, guaranteeing consistency, readability, and simple processing by totally different instruments and techniques. Organizations share this menace intelligence by numerous channels, together with electronic mail, file transfers, net platforms, or automated protocols like STIX and TAXII. Shared intelligence is then consumed, and applicable countermeasures are carried out based mostly on the insights gained.
Organizations collaboratively and constantly monitor the effectiveness of their menace intelligence sharing efforts, offering suggestions to one another and refining their processes to enhance the standard and relevance of the shared knowledge.
Advantages of collaborating in menace intelligence sharing
Simply as neighborhood watch packages promote involvement by group constructing, shared duty, and mutual profit, menace intelligence sharing packages encourage participation by doing the next:
- Elevating consciousness of the significance of collaboration and knowledge sharing in bettering a corporation’s safety posture.
- Establishing communication channels and platforms for sharing menace intelligence, equivalent to emails, net platforms, or automated protocols.
- Present steering and help to members by designated groups or people liable for managing the menace intelligence sharing program.
- Providing coaching and academic supplies on menace intelligence sharing greatest practices, instruments, and frameworks.
- Constructing relationships with {industry} companions like ISAC, or different menace intelligence sharing communities to alternate info and study from one another’s experiences.
- Encourages collaboration by pooling assets, data, and experience, collectively.
By enhancing group’s menace detection and response capabilities, their general safety posture and resilience towards cyberattacks will increase.
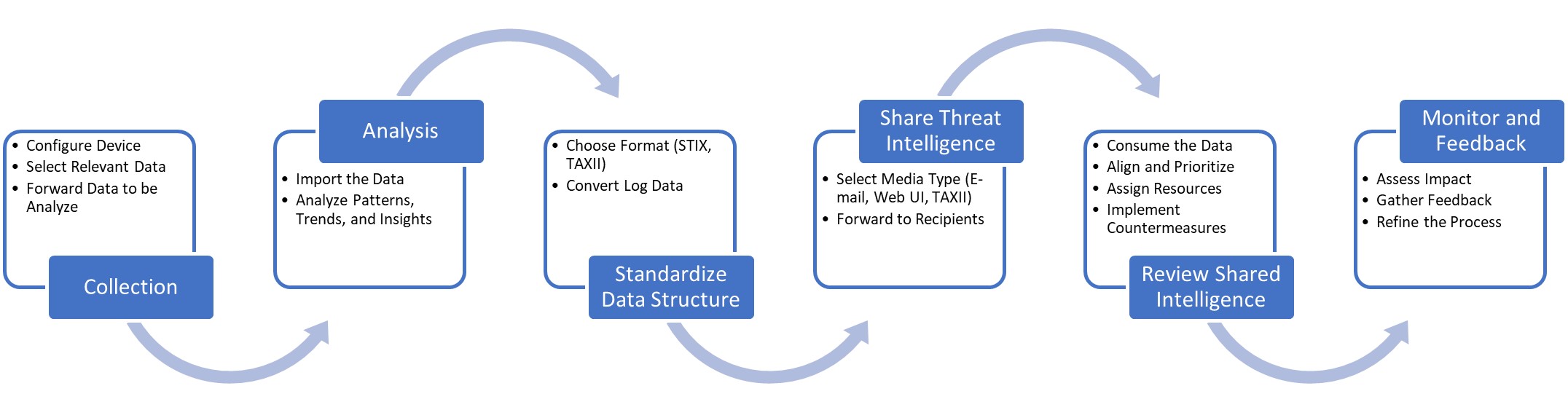
What the menace intelligence sharing course of appears like
![threat intelligence sharing process]()
Assortment
The method begins with the gathering of menace intelligence from a variety of sources, together with inner community logs, safety instruments, open-source intelligence (OSINT), business menace intelligence feeds, and industry-specific sharing communities or Data Sharing and Evaluation Facilities (ISACs).
Evaluation
The collected knowledge is then analyzed to establish patterns, tendencies, and actionable insights, serving to organizations higher perceive the menace panorama and make knowledgeable choices about their safety methods.
Standardize knowledge construction
To make sure consistency, readability, and simple processing by totally different instruments and techniques, the menace intelligence knowledge is structured utilizing standardized codecs and languages, equivalent to STIX or TAXII.
Share menace intelligence
Organizations improve their cybersecurity efforts by sharing menace intelligence. They will alternate info by numerous channels, equivalent to electronic mail, file transfers, net platforms, or automated protocols.
Evaluation shared intelligence
The shared intelligence is built-in into the receiving group’s safety infrastructure, equivalent to Safety Incident and Occasion Administration “SIEM” techniques, Intrusion Detection System/Intrusion Prevention System “IDS/IPS”, or Menace Intelligence Platforms “TIP”, and is used to tell safety methods, prioritize assets, and implement countermeasures.
Monitor and suggestions
Lastly, organizations constantly monitor the effectiveness of their menace intelligence sharing efforts, present suggestions to their companions, and refine their processes to enhance the standard and relevance of the shared knowledge.
Beginning your personal menace intelligence sharing program
Implementing a menace intelligence sharing program strategically bolsters the group’s safety posture and resilience towards evolving cyber threats. The next steps can be utilized as a framework create a menace intelligence sharing program:
- Perceive the basics of menace intelligence sharing, together with frequent frameworks and requirements like STIX and TAXII.
- Outline roles and obligations, workflows, and communication channels to raised implement and handle the menace intelligence sharing program.
- Assess your group’s particular menace intelligence sharing necessities, equivalent to the kind of menace knowledge you wish to share, the sources of this knowledge, and the specified degree of automation for sharing and consuming menace intelligence.
- Determine potential companions for sharing menace intelligence, equivalent to {industry} friends, ISACs, or business menace intelligence suppliers.
- Combine menace intelligence sharing capabilities into your current safety infrastructure, equivalent to safety info and occasion administration (SIEM) techniques, intrusion detection and prevention techniques (IDS/IPS), or menace intelligence platforms (TIPs).
- Develop inner processes and tips for creating, sharing, and consuming menace intelligence inside your group, together with roles and obligations, workflows, and communication channels.
- Repeatedly monitor the effectiveness of your menace intelligence sharing efforts, collect suggestions from members, and refine your processes to enhance the standard and relevance of the shared knowledge.
Overcoming the challenges of beginning a menace intelligence program
A number of {industry} requirements and compliance frameworks have printed or constructed into their packages the power to securely set up a menace intelligence sharing program for a corporation. NIST, ISO, FIRST, ENISA, and CIS all have insights, tips, and greatest practices associated to cybersecurity collaboration and knowledge sharing that may complement and help a corporation establishing a menace intelligence sharing program.
One of many key challenges is elevating consciousness and understanding of the advantages of menace intelligence sharing, together with the very best practices, instruments, and frameworks obtainable. Organizations can deal with this by complete coaching and academic supplies for his or her safety groups and stakeholders.
Organizations can foster a tradition of belief and collaboration by creating partnerships with {industry} friends, ISACs, or different menace intelligence sharing communities, emphasizing the mutual advantages of sharing and collaboration. Allocating mandatory assets, equivalent to personnel, know-how, and funding, is essential for establishing a sturdy menace intelligence sharing program. This may increasingly require acquiring government sponsorship and help to make sure organizational dedication and enough useful resource allocation.
Organizations deal with integration points by choosing instruments and platforms which can be suitable with their present techniques and help standardized codecs like STIX or TAXII. Additionally, organizations ought to spend money on adopting and implementing standardized frameworks, guaranteeing constant and readable knowledge throughout totally different instruments and techniques.
Guaranteeing the standard and relevance of shared knowledge might be addressed by implementing processes to filter out noise, validate the accuracy of shared knowledge, and prioritize essentially the most related threats. As well as, organizations that set up a steady suggestions loop to enhance the menace intelligence sharing program is essential. That is achieved by monitoring the effectiveness of this system, gathering suggestions from members, and refining processes to enhance the standard and relevance of the shared knowledge.
Conclusion
Cybersecurity menace intelligence sharing is a strong software for organizations to collaboratively deal with the challenges posed by an ever-evolving menace panorama. Just like the neighborhood watch, fostering a way of group, shared duty, and mutual profit, creates a powerful and efficient menace intelligence sharing program that enhances everybody’s general safety posture and resilience towards cyber threats.